NewEra Software is a proud sponsor of the zExchange - A community of z/OS Citizens
OUR GOAL? Support & maintain system Integrity
ICE/Applications - built, distributed & supported by NewEra Software, Inc
NewEra Software is a proud sponsor of the zExchange - A community of z/OS Citizens
ICE/Applications - built, distributed & supported by NewEra Software, Inc
ICE/TCE provides the operational balance needed between systems programmers, who must have access to critical z/OS resources, and the desire of security officers, compliance managers, and auditors, to establish effective management controls – controls that monitor for compliance, that detect and report changes.

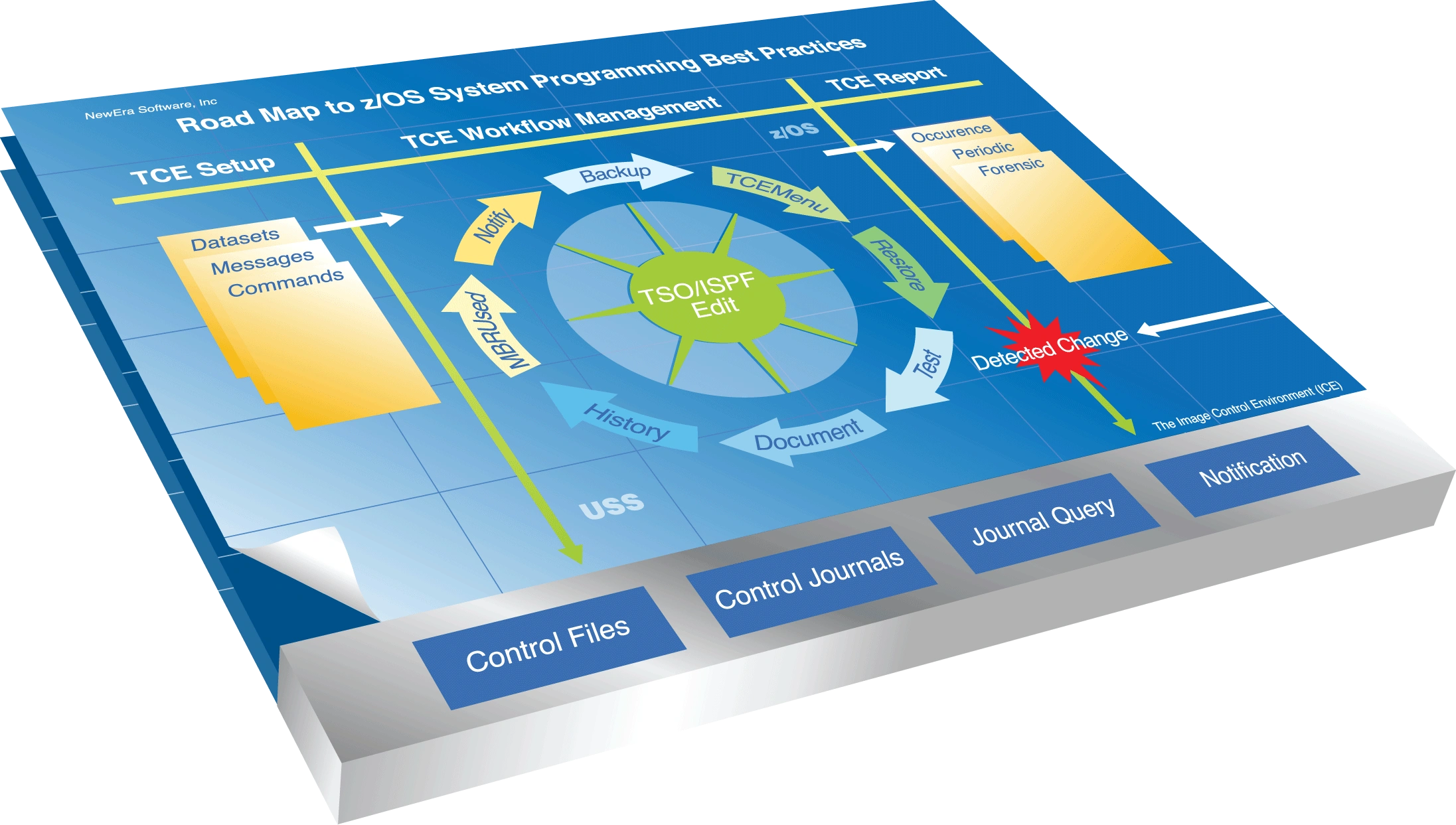
ICE/TCE is a z/OS system software utility designed to assist z/OS System Programmers who are charged with the responsibility of supporting and maintaining the z System environments. It's intuitive, easy to use 3270 interface provides ISPF access to critical z/OS system configuration datasets. It tracks and logs their work every step of the way, assuring them of the availability of automatic backups should recovery become necessary.
ICE/TCE manages access controls at both the dataset and member level, creating a secondary layer of control, augmenting that provided by the External Security Manager(ESM). Many, in management, considered it a ‘Compensating Control’, filling a long-standing functional gap between conventional Change Management Tools and the ESM.
ICE/TCE is fully under the control of the z/OS Administrator. Using a 3270 Interface, Control Boundaries (Categories, Datasets, Commands, System Messages, LOAD Libraries and UNIX files) are easily defined. Within each boundary, agents are vigilantly checking access rights and recording changes. Changes, even those made outside the TSO/ISPF domain, are captured and reported. All changes are permanently stored in Control Journals for use in interactive or batch Forensic and Periodic Management Reports.
ICE/TCE can operate, at the user’s direction, as a tool active on each LPAR, tracking, controlling, and reporting activity that occurs on that LPAR. It can also operate on a SYSPLEX-wide basis, monitoring and controlling all activity occurring on all LPARS within a SYSPLEX.
ICE/TCE provides Automatic Backups, Change History, Restore Points, Component Inspection, Change Impact, Change Descriptor, Member Level, and JOB Submission Control, all of which is designed to reinforce existing ESM defined access boundaries.
ICE/TCE allows your team to maintain the highest levels of internal control as demanded by regulation and/or your own best practices. In doing so, ICE/TCE addresses the most basic issues associated with internal control over the z/OS configuration - namely, WHO is making changes - with all the attendant detail: the what, when, where, and how.
Your team's work is managed and fully documented. You're in control: no ifs, no ands, no buts.
The support and maintenance of z/OS is complicated. Fortunately, sound z/OS systems programming best practices are well known and straightforward. But we’re all human, all busy, we all forget and our best intentions to conform to these practices will sometimes go unfulfilled.Does your team always:
This could be a real problem. No Backup, no Test, no Review, no Documentation, no Notification. Any of these can lead to a loss of z/OS configuration integrity or compliance or worse - to a loss of z/OS availability.
ICE/TCE is the System Software Utility that enhances the use of TSO/ISPF for experience System Programming Staff by fully automating, step-by-step, the individual tasks that will lead them to compliance with the best z/OS systems programming practices. Those new to z/OS System Programming will come up to speed sooner, develop greater confidence in their skill, make fewer mistakes. We all do! ICE/TCE can help to reduce the impact on system operations.
ICE/TCE enhances the TSO/ISPF experience for z/OS System Programmers by fully automating, step-by-step, the individual tasks that will lead them to compliance with the best z/OS systems programming practices.
ICE/TCE strikes a balance in design and implementation between the need for enhanced productivity and the control remediation needs of z/OS System Administrators by compensating for acknowledged weaknesses in their Legacy Security Manager Processes. Consider the following:
These examples are but a few of a growing list of issues that inch us ever closer to a state of non-compliance and insecurity when actual control over z/OS configuration changes is brought into question. All speak to a need for the collection and reporting of configuration event detail beyond that supported by legacy systems, for example, the System Management facility (SMF) and conventional Change Management processes.
These examples demand answers to the questions of responsibility and accountability between colleagues and consultants and speak to the need for enhanced z/OS configuration control - control within the dataset boundaries provided by Legacy Security; control that focuses on the individual configuration members that ensure the integrity of your z/OS environment.
ICE/TCE, resolves these issues, fully supports existing Legacy Security and extends the z/OS security and control boundaries to heretofore unrecognized events, capturing and reporting them as they occur in real time, enforcing Library and Member Level control over both authorized and unauthorized catalog actions and member updates/reads.


Contractors come and go here all the time. We give them pretty much the same access we give to our own system staff. Until we began using ICE/TCE, we had no idea what they were actually doing. Now we do. ICE/TCE reporting and query functions resolved this completely. I now know who did what, to what, and when.

We give operators access to MVS commands for dynamically reconfiguring z/OS. We were hesitant to use strict COMMAND class control for fear of locking them out. Now, leveraging the recording of commands provided by ICE/TCE, we have a way to capture what they are doing. No lockouts; all changes are now fully documented.

I cannot tell you how many times I have had to get involved in a system security dispute between my Security Officer and System Programming Manager. Both are well-intended: one wants more security of z/OS system changes, the other says ‘no way’. The Control Editor resolved this for me, for us. It was easy to set up, a snap to learn.
ICE/IFO, like all NewEra Software Products, is licensed on an MSU, tiered price scale,
for a defined term or in perpetuity by CPU, Site, Region or Globaly.
Maintenance is included in the first license year and thereafter is 15% of the then current list price.
8070 Santa Teresa Blvd, Suite 240, Gilroy, California 95020, United States
Copyright © 2018 NewEra Software, Inc. - All Rights Reserved.
Powered by GoDaddy